- Home
- Hardware
- SDKs
- Cloud
- Solutions
- Support
- Ecosystem
- Company
- Contact
news
Launching the ESP Privilege Separation
Shanghai, China
Aug 5, 2022
ESP Privilege Separation is designed to prevent user-facing applications from interfering with protected applications and code.
Espressif Systems (SSE: 688018.SH) is pleased to announce the release of a new feature, ESP Privilege Separation, which is designed to boost security by preventing user applications from interfering with protected applications.
Traditionally, any ESP-IDF application on an Espressif SoC is built as a single monolithic firmware without any separation between the “core” components (Operating System, Networking, etc.) and the “application” or “business logic”. In the ESP Privilege Separation framework, we split the firmware image into two separate and independent binaries, that is, protected and user applications.
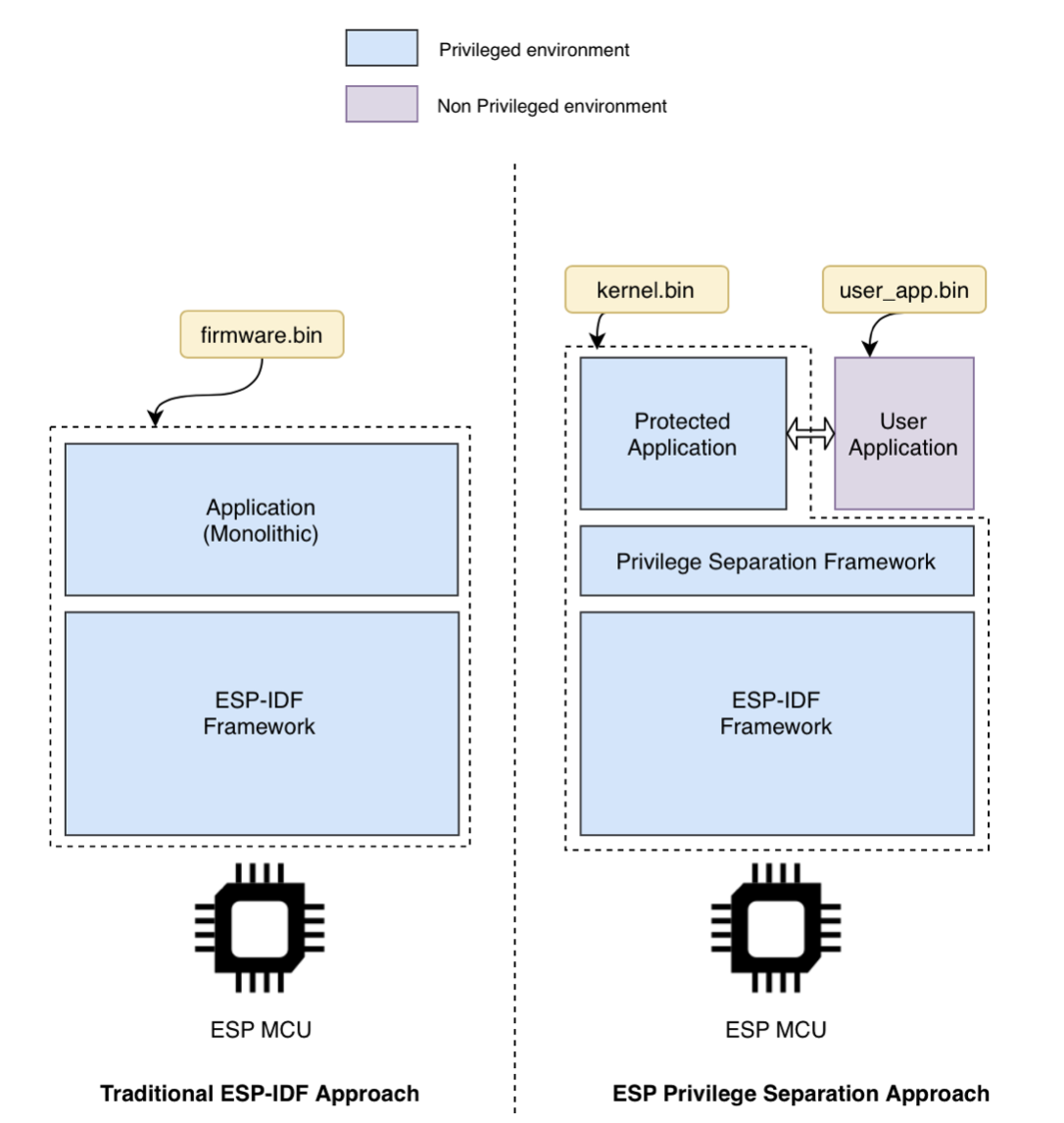
ESP-IDF projects can now use a privilege separation framework to prevent user-facing code from meddling in protected code.
As Hackster’s technical writer, Gareth Halfacree, notes: “The result, which places the new Privilege Separation Framework above the ESP-IDF framework, is the creation of two isolated execution environments: the user and the kernel (or privileged) application. User-facing applications are isolated from the kernel application, thus boosting security and ensuring that bugs in the ‘business logic’ will not affect the whole system, since they can be readily caught and diagnosed —even remotely.”
The framework allows for other possibilities, too: Over-The-Air (OTA) updates can be issued for either or both isolated environments entirely independently. Additionally, any required certifications to the protected application can be applied for only once, regardless of the number of updates issued to the user-facing code. This allows for multiple user-facing applications to be chosen and called from within the single protected application.
ESP Privilege Separation is currently exclusive to ESP32-C3. In fact, we started off with a proof-of-concept based on ESP32, but we soon realized that ESP32 would require robust hardware support, in order for it to allow permissions at the hardware level and achieve the desired isolation between the user and the kernel application. This led us to design our own custom peripherals for ESP32-C3 and, eventually, Espressif’s new framework, ESP Privilege Separation. You can read all the technical details about it in The ESP Journal, Espressif’s official technical blog. There you can also find a whole case study on the ESP Privilege Separation.
ESP Privilege Separation is currently exclusive to ESP32-C3
Getting Started
Please note that this project is still in its beta phase and, therefore, under development. There are certain limitations and bottlenecks which are constantly being addressed. So, please report any issues or bugs you may encounter.
The framework is entirely open-sourced and can be found in our ESP Privilege Separation repository. For a detailed technical documentation about it, please click on here.
Also, feel free to report any issues by raising an issue tracker on our GitHub repository. We also welcome contributions to this framework through PRs.
We hope that the ESP Privilege Separation proves to be a novel approach in application development which will open various avenues of creativity for you. We are eager to hear your thoughts about this.


 LinkedIn
LinkedIn 微信
微信
 Twitter
Twitter Facebook
Facebook
